QUESTION 54
Which of the following nmap parameters scans a target for open TCP ports? (Choose two.)
Explanation
The nmap command is a network exploration and security auditing tool that can scan hosts and networks for open ports, services, operating systems, vulnerabilities, and other information. The nmap parameters that can scan a target for open TCP ports are:
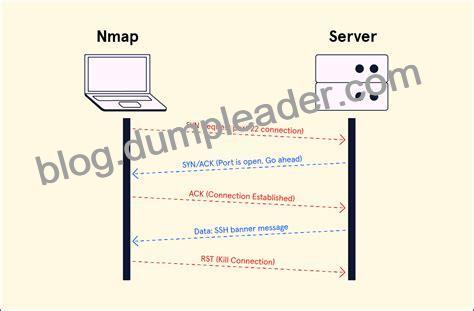
-sT: This parameter performs a TCP connect scan, which establishes a complete connection to the target host by completing a TCP three-way handshake. This is the default scan type when the user does not have root privileges. The advantage of this scan is that it works on any system that supports TCP, but the disadvantage is that it is easily detectable by firewalls and intrusion detection systems.
-sS: This parameter performs a TCP SYN scan, which sends a TCP SYN packet to the target port and waits for a response. If the response is a SYN/ACK packet, the port is open. If the response is a RST packet, the port is closed. This scan does not complete the TCP three-way handshake, so it is faster and stealthier than the TCP connect scan. However, this scan requires root privileges and may not work on some systems that do not follow the TCP standard.
The other parameters are not related to TCP port scanning:
-sO: This parameter performs an IP protocol scan, which sends IP packets with the specified protocol number set in the IP header. It can be used to determine which IP protocols are supported by the target host.
-sZ: This parameter is not a valid nmap parameter and will cause an error.
-sU: This parameter performs a UDP scan, which sends a UDP packet to the target port and waits for a response. If the response is an ICMP port unreachable message, the port is closed. If the response is a UDP packet, the port is open. This scan can be used to find open UDP ports, which are often used by DNS, SNMP, DHCP, and other services.
References: LPIC-2 202 exam objectives, LPIC-2 202-450 Exam Prep: Network Configuration, Nmap Tutorial: Common Commands, Nmap Scan Types Cybersecurity | Nmap | TCP Connect Scan | Codecademy